Posts filed under ‘Windows 2012’
How to install and configure LAPS
Recently , we had to deploy LAPS on one of our client environment. The requirement was to manage the local administrator password of all the domain joined workstations / servers via centrally. I used the below guides to complete the installation .(Kudos to the blog owners)
Source1:
https://scripting.rocks/sysadmin/laps/
Source2:
https://vaishnaav.files.wordpress.com/2019/12/step-by-step-guide-to-deploy-microsoft-laps-1.pdf
(via :prajwaldesai.com).
In addition to the above you may come across the below issues.
- Unable to configure the Group Policy using the LAPS Administrator Template or missing LAPS Administrator Templates.
Solution: You need to run the laps installation on the DC and remove all the options and select only ” GPO editor templates” - Manual Password reset via Fat Client / Command Line is not working.
Solution : You need to run the GPupdate after the manual password reset on the computer where you are changing the password.
Good Luck.
SYSVOL Replication Error on Windows 2012 R2
Hi Guys
Recently we migrated one of our customer’s active directory domain controllers to a virtualized environment. During the DC migration my colleague noticed that the SYSVOL and NETLOGON folders are not replicating it’s contents from the existing domain controller. Thus he copied the contents manually. But after some time client started reporting error like;
- The Group Policy is not getting updated or Propagated to all the workstations / users.
- Logon Scripts stopped working.
Thus when we digged in to the problem we were able to track down the issue to DFSR based sysvol replication, Most importantly the old DC was not replicating for almost 1300 days approximately(Figure.1) The below event ID’s helped us to track down the issue:
So when we started troubleshoot we tried to ran the commands stated in the Eventviewer(refer attached file) but no avail.
Also we ran the below command
For /f %i IN (‘dsquery server -o rdn’) do @echo %i && @wmic /node:”%i” /namespace:\\root\microsoftdfs path dfsrreplicatedfolderinfo WHERE replicatedfoldername=’SYSVOL share’ get replicationgroupname,replicatedfoldername,state
(In case if you ran in to an error when running the above command it could be due to the ‘ is get changed to ` when copying and pasting it. Thus change it manually)
Strangely the status on all the server showing 2 which is Initial Sync. (One of the reason for the problem) .Also in our MaxOfflineTimeInDays more than 1000 days. But
By default in Windows the is set to 60 Days. In our case we need to extend it upto 1800 days where there was an offset of more than 1000. so we ran the command to force the servers to allow the content freshness for more than 1000 days.
wmic.exe /namespace:\\root\microsoftdfs path DfsrMachineConfig set MaxOfflineTimeInDays=1800
(Do not forget to bring it back the original value of 60 Days)
But sill no avail. Then we decided to Authoritative restore of the SYSVOL folders. We ran the below command set which were extracted from the MS KB:https://support.microsoft.com/en-us/help/2218556/how-to-force-an-authoritative-and-non-authoritative-synchronization-fo)
Do this step on the PDC Emulator Role
Stop the DFSR Service
#net stop dfsr
Open the ADSIEDIT.MSC tool, connect to the “Default Naming Context” and move to OU=Domain Controllers” and select the PDC Emulator –> CN=SYSVOL Subscription,. Right click on CN=Domain System Volume and go to Properties(preferably the PDC Emulator, which is usually the most up to date for SYSVOL contents): and modify the following DN and two attributes
msDFSR-Enabled=FALSE
msDFSR-options=1
Modify the following DN and single attribute on all other domain controllers in that domain:(Using the same path as mentioned above)
msDFSR-Enabled=FALSE
Stop the DFSR service on all the remaining controllers
#net stop dfsr
Force Active Directory replication throughout the domain and validate its success on all DCs.
#repadmin /syncall /AdP
Start the DFSR service set as authoritative:(On the PDC emulator)
#net start dfsr
You will see Event ID 4114 in the DFSR event log indicating SYSVOL is no longer being replicated.
On the same DN from Step 1, set:
msDFSR-Enabled=TRUE
Run the below command to force Active Directory replication throughout the domain and validate its success on all DCs.
#repadmin /syncall /AdP
Run the following command from an elevated command prompt on the same server that you set as authoritative:(In order to run the below command you need to install the “DFS Management Feature” on the servers , not the DFS Role)
DFSRDIAG POLLAD
You will see Event ID 4602 in the DFSR event log indicating SYSVOL has been initialized. That domain controller has now done a “D4” of SYSVOL.
Start the DFSR service on the other non-authoritative DCs.
#net start dfsr
You will see Event ID 4114 in the DFSR event log indicating SYSVOL is no longer being replicated on each of them.
Revert the the following DN attribute as it was , on all other domain controllers in that domain.
msDFSR-Enabled=TRUE
Run the following command from an elevated command prompt on all non-authoritative DCs (i.e. all but the formerly authoritative one):
DFSRDIAG POLLAD
————————————————————————————-
Voila we could see the replication started working and when we checked the replication status via the command
For /f %i IN (‘dsquery server -o rdn’) do @echo %i && @wmic /node:”%i” /namespace:\\root\microsoftdfs path dfsrreplicatedfolderinfo WHERE replicatedfoldername=’SYSVOL share’ get replicationgroupname,replicatedfoldername,state
(In case if you ran in to an error when running the above command it could be due to the ‘ is get changed to ` when copying and pasting it. Thus change it manually)
OR
dfsrmig /getglobalstate
it shows the status 4 (which is all synced)
I am listing the below articles which helped me in the initial troubleshooting.
http://www.itprotoday.com/windows-8/fixing-broken-sysvol-replication
http://kpytko.pl/active-directory-domain-services/non-authoritative-sysvol-restore-dfs-r
http://kpytko.pl/active-directory-domain-services/authoritative-sysvol-restore-dfs-r/
Good Luck
Muralee
Update 1 (29/01/2018) :
- Added the start and stop DFSR commands.
How to import Users to Windows 2012 Active Directory using PowerShell
Hi Guys
In many AD installations I do come across requirements to create multiple users in Active Directory(More than 200 in many cases) .In these cases we could use the below mentioned CSV template and use the PS command to directly import the users in to Active Directory.
Here the Path value is pointing to the OU that you want to place the users in the Active Directory , which could be find using the Attribute Editor of the OU(We need to enable the Advance Feature in the ADUC Management Console)
PS Command Syntax
Import-CSV C:\anyname.csv | New-ADUser –AccountPassword (ConvertTo-SecureString –AsPlaintext “any complex password” –Force) –PassThru | Enable-ADAccount.
Example:
Import-CSV C:\Users_1.csv | New-ADUser –AccountPassword (ConvertTo-SecureString –AsPlaintext “P@ssw0rd” –Force) –PassThru | Enable-ADAccount
Update2:
I am including here another method to achieve the same.
# Prepare the CSV file as per below(You could any details as much as you want, by adding the correct attribute.)
firstname,lastname,username,email,department,password,jobtitle,company,ou,Mobile
# Then run the below powershell.
+ You must change the active directory domain name.
+ You must change the csv file name.
+ Ensure that , you have given the proper DN namespace for the OU Value. Otherwise , the script will fail with the below error messages:
“No superior reference has been configured for the directory”
“New-ADUser : The object name has bad syntax”
===================================================================================
# Import active directory module for running AD cmdlets
Import-Module activedirectory
#Store the data from ADUsers.csv in the $ADUsers variable
$ADUsers = Import-csv C:\test.csv
#Loop through each row containing user details in the CSV file
foreach ($User in $ADUsers)
{
#Read user data from each field in each row and assign the data to a variable as below
$Username = $User.username
$Password = $User.password
$Firstname = $User.firstname
$Lastname = $User.lastname
$OU = $User.ou #This field refers to the OU the user account is to be created in
$email = $User.email
$telephone = $User.Mobile
$jobtitle = $User.jobtitle
$company = $User.company
$department = $User.department
$Password = $User.Password
#Check to see if the user already exists in AD
if (Get-ADUser -F {SamAccountName -eq $Username})
{
#If user does exist, give a warning
Write-Warning “A user account with username $Username already exist in Active Directory.”
}
else
{
#User does not exist then proceed to create the new user account
#Account will be created in the OU provided by the $OU variable read from the CSV file
New-ADUser `
-SamAccountName $Username `
-UserPrincipalName “$Username@vands.pro” `
-GivenName $Firstname `
-Surname $Lastname `
-Name “$Firstname $Lastname” `
-DisplayName “$Lastname, $Firstname” `
-Enabled $True `
-Path $OU `
-Company $company `
-EmailAddress $email `
-Mobile $telephone `
-Title $jobtitle `
-Description $jobtitle `
-Department $department `
-AccountPassword (convertto-securestring $Password -AsPlainText -Force) -ChangePasswordAtLogon $True
}
}
===============================================================================
There is no certificates installed on this remote desktop server
On the RD Session Host Configuration when you tried to assign the SSL certificate which you obtained from any vendor you will receive the message in the title.
This is because the SSL certificate need to be imported on .PFX format , In my case the cert i downloaded from GoDaddy was having a .crt extension. Therefore I opened the Certificate-Snapin(Local Computer) and selected the already imported certificate in the Personal container,then I tried to export the certificate as Personal Information Exchange(.pfx)so I could re-import it correctly But I was not able to do so as it was showing the below screen,
As you see the Personal Information Exchange option is disabled as this is because the SSL certificate does not have the private key.
In order to overcome this get the serial number of the certificate(Open the ssl certificate by double clicking on it and open the details TAB) then on a command prompt entere the below command;
certutil -repairstore my “SerialNumber”
That’s it now you could the export the cert as .pfx and re-import it on Personal and Remote Desktop containers in Certificate Snap-in.
Finally you could select the SSL on RD Session Host configuration.
Source:
http://scexblog.blogspot.com/2010/09/export-personal-information-exchange.html
Update1:
In 2012 and above MS have removed the RDP Snap-in to change the SSL Certificate thus you need to follow the steps mentioned in MS KB Article:https://support.microsoft.com/en-us/help/3042780/remote-desktop-listener-certificate-configurations-in-windows-server-2
Inaccessible boot device on Windows 2012 with EMC Networker
Hi
I would like to share my experience related to the above error.
Recently we received a call from our customer saying that 2 VM’s were not booting. We were in panic mode as these 2 servers are the domain controllers and the backup software which was supposed to do the BMR also failing.
Thereafter when we contacted Microsoft Support the team identified the error is due to the “nsrbbwi” key which being added on the Registry by our EMC Networker Backup Tool and once it was removed the servers booted normally.
Go to the below Registry via the Command Prompt from the System Recovery Options
ControlSet001\Control\Class\{533C5B84-EC70-11D2-9505-00C04F79DEAF}
ControlSet001\Control\Class\{71A27CDD-812A-11D0-BEC7-08002BE2092F
Remove the Value for “Upperfilters” as it will be pointed to “nsrbbwi”
Reboot the server.
Source:-
-Microsoft PSS
-https://blogs.technet.com/b/mrmlcgn/archive/2014/02/20/after-installing-upgrading-emc-networker-version-8-1-1-windows-fails-to-boot-stop-error-7b-quot-inaccessible-boot-device-quot.aspx
Best regards
How to reinstall the failed Additional Domain Controller on Windows 2012
Hi Folks
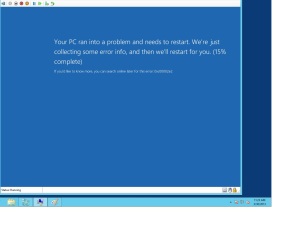
Recently I faced an issue with a customer where we have installed a Windows 2012 Additional Domain Controller as a Virtual Machine on Hyper-v Server , he was getting the below error.
So I was trying with all the CHKDSK , Last Known Good Configuration , Directory Restore mode BUT everything failed, Including the below suggestion on Technet forums
Since I had to meet the SLA on solving the ticket , I decided to re-install the Additional Domain Controller on the same name ,which will avoid me of Cleaning the metadata and other complex task.
So I performed the follow steps.
- Re-installed the Windows 2012 Guest on Hyper-V
- Change the name to my previous Additional Domain Controller name.
- Open the Powershell
- Add-WindowsFeature AD-Domain-Services –> This will install the Active Directory Domain Services.
- Import-Module ADDSDeployment
- Install-ADDSDomainController -AllowDomainControllerReinstall -Credential (Get-Credential) -DomainName “test.local”This will prompt you to enter the credential , make sure you enter the credential either in DOMAINNAME\Administrator OR Administrator@DOMAINNAME
Secondly it will prompt you to enter the Directory Restore Password - That’s all it will promote the new server as a domain controller , you do not need to do anything on DNS or other related services.
- Finally you will need to install the ADDS Management Tools to Manage the Active Directory components you could do it via PowershellImport-Module ServerManager
Add-WindowsFeature RSAT-AD-PowerShell,RSAT-AD-Tools and hit enter
OR via the GUI
Voila… My problem was solved . Good luck Guys….